Caesar encryption online
Simply explained and directly applied!
Discover the world of Caesar encryption!
Ever since people have been communicating with each other, there has been a need to protect secret messages. Even in ancient times, encryption techniques were used to conceal military and diplomatic messages from the eyes of the enemy. Cryptography, the science of encryption, played a decisive role in wars and political intrigues and continued to develop over thousands of years. Learn about the Caesar encryption technique on this page, which was named after Julius Caesar, who used this technique in ancient Rome.
How does Caesar encryption work?
Caesar encryption is one of the oldest and simplest encryption methods. It was named after Julius Caesar, who used it to encrypt secret military messages. The method is based on a simple shifting of the letters in the alphabet.
In the Caesar cipher, each letter in plain text is shifted a certain number of places in the alphabet. The number of digits is called the key.
Example with a shift of 3 digits:
Plain text: HELLO Encryption: KHOOR
– H → K
– E → H
– L → O
– L → O
– O → R
This means that each letter is three places further on in the alphabet. When the end of the alphabet is reached, it starts again from the beginning.
Caesar encryption online
With the small app you can try out CAESAR encryption for yourself.
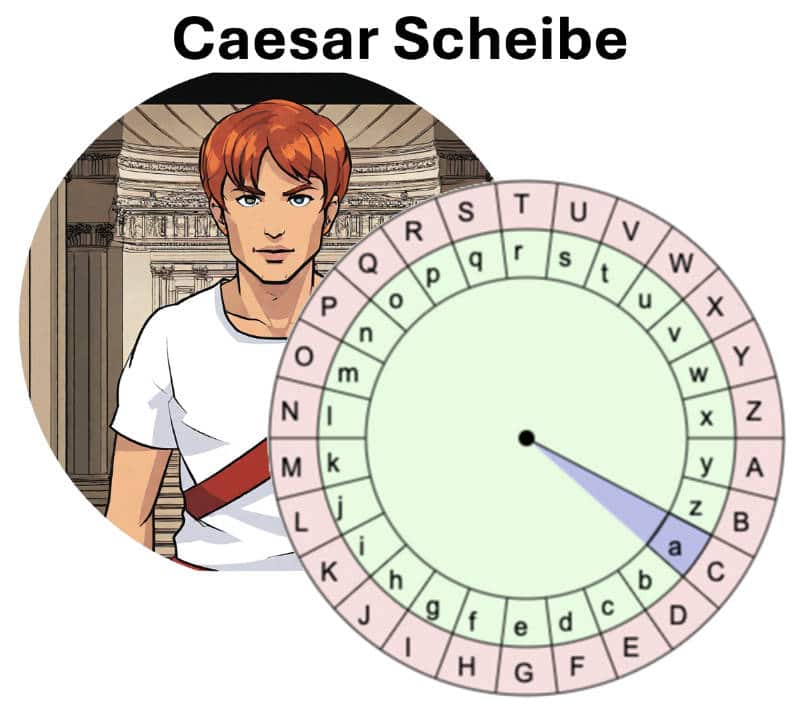
And this is how Caesar encryption works online with the Caesar disk:
- Turn the Casear disk to the left or right.
- The outer ring shows the unencrypted letters.
- The inner ring contains the shifted new letters of the encoded message.
- Enter the message in the field below the disk.
- Click on the “Verschlüssele” button to encode the message with the Caesar Chiifre.
- The Caesar-encoded text is then displayed in the “Encoded text” field.
A,B,C: Letter Original
a,b,c: Letter encrypted
Caesar encryption
Encrypted text:
Security of Caesar encryption
To decrypt a Caesar-encrypted message, the process is simply reversed by shifting the letters back the same number of places.
The Caesar cipher is very uncertain because there is only a limited number of possible shifts (maximum 25).
An attacker can simply try all possible shifts (so-called brute force attacks) to find the plaintext.
Why is Caesar encryption still important?
Although it is no longer used for secure communication today, the Caesar cipher is one of the foundations of modern cryptography. It shows how encryption works and is often used to explain the principle of secret messaging.
✅ Caesar encryption is simple and historical.
✅ It works by shifting the letters in the alphabet.
✅ It is easy to crack, but important for understanding cryptography.
✅ It was one of the first encryption methods and was used by Julius Caesar.
Caesar encryption Python code
Would you like to write your own program in Python to run a Casear code? Here we have created a small Python program for you.
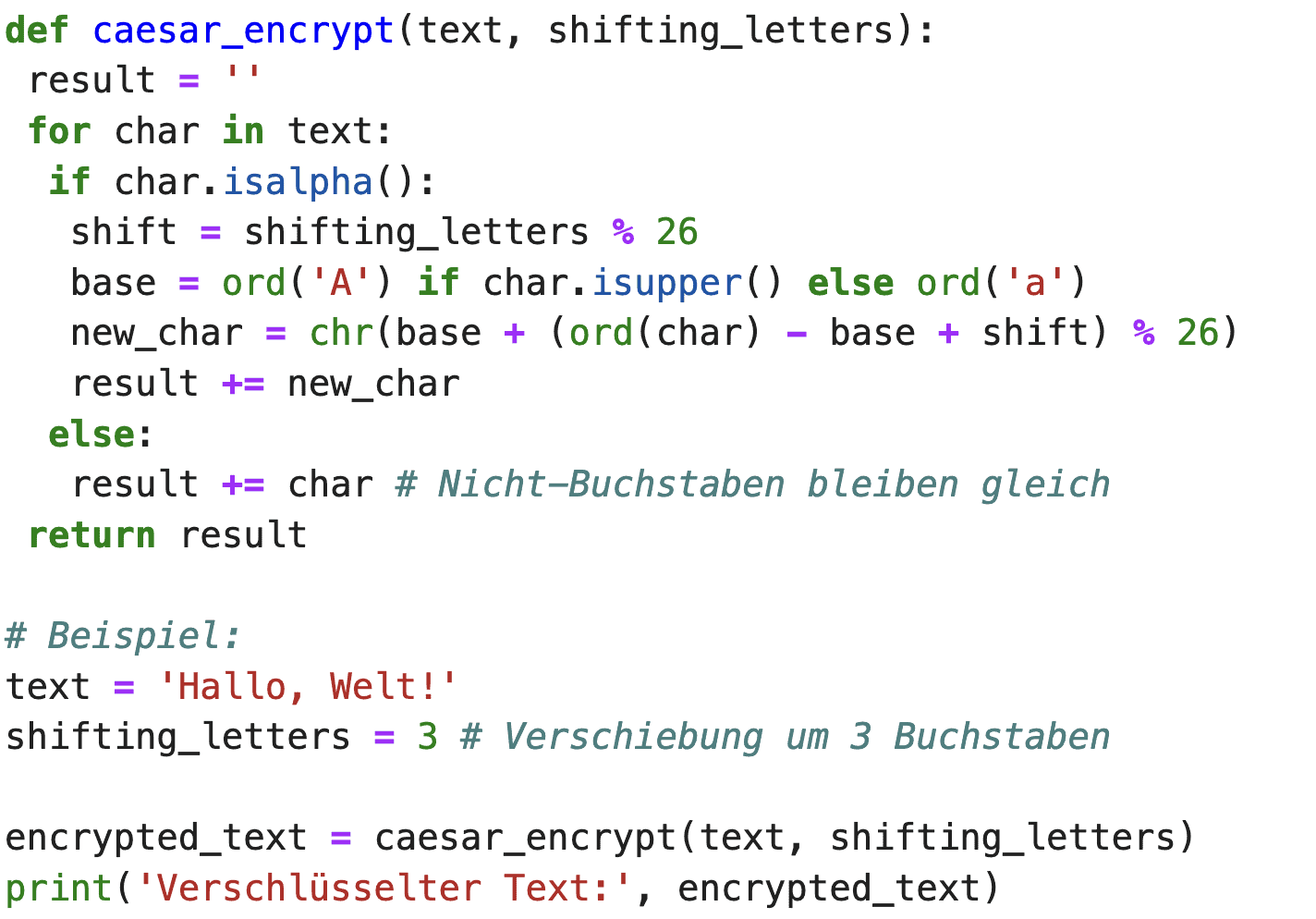
We have intentionally only included an image of the Python code above, as otherwise the indentation with spaces is not properly visible in our web application. However, you can download the code as a txt file!
Explanation of the Python program for Caesar encryption:
- Only letters are moved (upper and lower case letters are treated separately).
- Other characters (spaces, punctuation marks, numbers) remain unchanged.
- The modulo operation
% 26ensures that the shift remains in the 26-letter alphabet.
FAQ – Caesar Code simply explained
What is Caesar encryption?
Caesar encryption is a simple, classic encryption method in which each letter in the alphabet is shifted by a fixed number of digits.
How does Caesar encryption work?
Each letter in a text is replaced by a different letter, which moves a fixed number of places to the right or left in the alphabet.
Why is it also called the "Caesar cipher"?
It is named after Gaius Iulius Caesar who is said to have used this method to encrypt military messages.
What does "shift" mean in Caesar encryption?
The shift indicates by how many positions each letter is moved forwards or backwards in the alphabet. For example, a shift of 3 results in A → D, B → Eetc.
Which letters are changed during encryption?
Only letters of the alphabet are moved, while numbers, spaces, punctuation marks and special charactersremain unchanged.
Are numbers, punctuation marks and spaces retained?
Yes, all non-letters such as numbers (1, 2, 3), punctuation marks (. , ! ?) and spaces are retained and are not changed.
How do you decrypt a text encoded with Caesar encryption?
To decode, simply move the shift in the opposite direction. opposite direction the same number of places backwards in the alphabet.
Can Caesar encryption be broken with a computer?
Yes, she is extremely insecureas there are only 25 possible shifts. A computer can try out all possibilities and quickly recognize the correct one.
Is Caesar encryption secure?
No, it can easily be determined by simple trial and error or a frequency analysis and is no longer used for real encryption today.
Which modern encryption methods are more secure than the Caesar cipher?
Methods such as AES (Advanced Encryption Standard), RSA encryption and elliptic curve cryptography offer a much higher level of protection today.
What historical examples are there of the use of Caesar encryption?
Julius Caesar is said to have used it in his campaigns, and it was still used in earlier centuries for simple secret messages.
What language influences are there in the Caesar cipher (e.g. umlauts in German)?
Umlauts like ä, ö, ü and the ß are not included in the classic Caesar cipher and would either have to be removed or replaced by ae, oe, ue, ss be replaced.
Practice encrypting Caesar texts

Continue playing and practicing Caesar encryption online with our online program!


